The concept behind Yoggie Gatekeeper™ is providing traveling laptops with the same level of security as within the corporate network. But how can one make a server room full of security appliances available to traveling users?
A powerful security processor
To make this possible Yoggie has invested two years in the development of a miniature security processor. The concept of specialized processors is not new. During the 80’s the mathematical processor was introduced. According to this concept when complex calculations were needed, a specialized mathematical processor would perform these tasks, effectively offloading these specialized tasks from the main processor. During the last 5 years, the same revolution took place with the introduction of a specialized network processor that would free the main processor from networking tasks.
Yoggie’s miniaturized security processor is as powerful as a Pentium III processor (520 Bps). It continues the trend of offloading specialized tasks from the main processor, for performance. But one of the main advantages of the specialized security processor relates to security.
Physical Separation
Unlike security software installed on the laptop, the Yoggie Gatekeeper uses the same approach that is used to protect the corporate network – physical separation of the first line of defense. A robust security appliance, with a hardened Linux-based OS, Yoggie Gatekeeper physically isolates the laptop from incoming Internet threats. The fact that Yoggie Gatekeeper is in the front-line instead of the laptop itself means it can protect from unknown attacks, dropping the connection as they are identified. If for any reason, the attack is successful, Yoggie Gatekeeper is hit first and will not allow further damage to the laptop.
Hardware Designed for Security
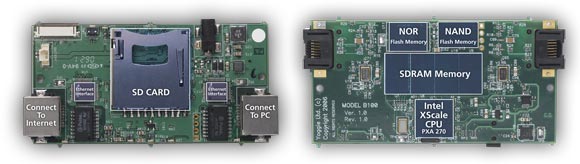
Yoggie Gatekeeper’s hardware was designed specifically for security purposes only. It includes a robust computing platform with a powerful CPU, with the sole purpose of protecting the laptop. Two separate network cards provide a physical separation between the unsafe zone (Internet) and the safe zone (connected to your laptop). The device also includes two separate Flash memory units. One unit stores a secured copy of the Linux OS. During pre boot, Yoggie copies the OS onto the second unit, and uses it during runtime. The original copy of the OS, stored on the first unit, does not include any “Write Access” permissions. This double-step process, guarantees that in the event of a successful attack, upon rebooting the device a clean and safe version of the OS is uploaded, making the OS and security applications completely safe.
Corporate-Grade Security Solutions
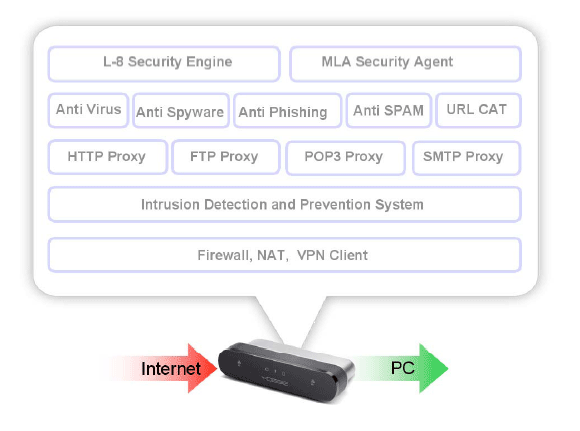
Yoggie Gatekeeper combines best-of-breed enterprise-class software with proprietary patent pending developments to provide a comprehensive security solution. With its stateful inspection firewall and NAT, Yoggie hides the laptop’s IP address from the outside world and closes any unnecessary network connection. In addition, the hardware design and hardened OS prevents any tampering on the Firewall (a common Spyware, Viruses behavior). Deep packet inspection is performed by a robust intrusion detection/prevention solution to detect attacks as they begin their operation.
The application layer includes four transparent proxies, two for web traffic (HTTP, FTP) and two for email traffic (SMTP and POP3). Using a powerful true-type detection engine, the proxies can deal with any content type, including decompiled elements such as compressed class and file attachments. These elements are analyzed by seven security agents:
- Multi-Layer Security Agent™
- Layer-8 Security Engine ™
- URL Categorization & Filtering
- Anti-Spam
- Anti-Phishing
- Antispyware
- Antivirus
- Transparent Email Proxies (POP3; SMTP)
- Transparent Web Proxies (HTTP; FTP)
- Intrusion Detection System / Intrusion Prevention System
- VPN Client
- Stateful Inspection Firewall
|
